Nobody likes being tracked. Still, most people store a detailed account of their movements on their phones, often shared with multiple apps. If you can get access to some of these user accounts you can track their whereabouts down to a relatively detailed level. In real time.
Tracking People – Google Maps Style
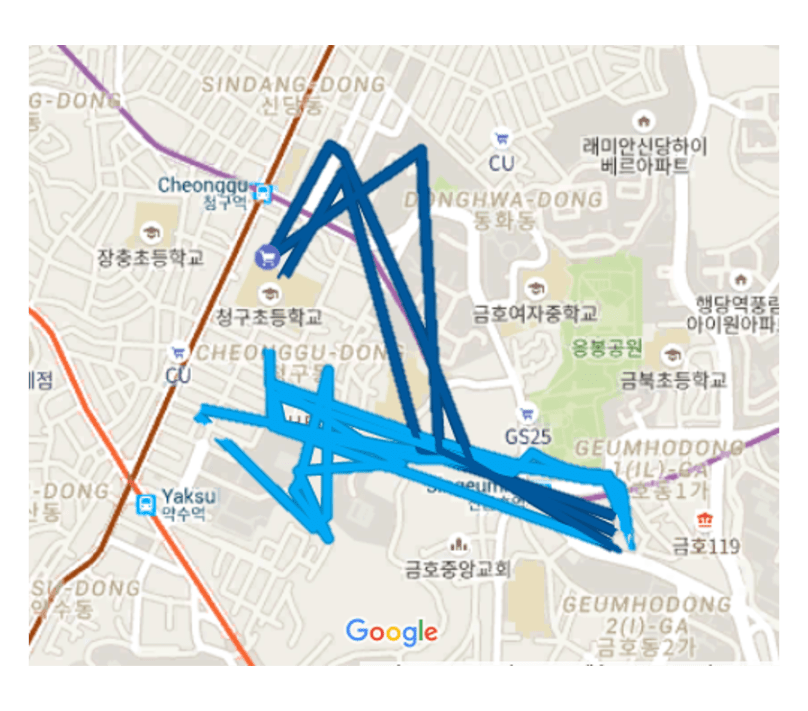
I have a 9-year old son, and one night I was watching the news with him. There was one story that got him curious, and almost angry, and rightly so. It was about a smartwatch for kids that was becoming popular as a gift from parents. This particular smartwatch allowed surveillance of the kids’ whereabouts via GPS, and they could also call their kids on the watch instead of giving them a phone. Parents can also turn on a one-way audio channel that allows them to eavesdrop on their kids’ conversations. My son told me he thinks this is unfair and outrageous – and I completely agree. He felt somewhat better when I told him that he is not going to get a watch like that (he has an analog wristwatch, a ting with no internet). More kids should care about privacy too.
Note to parents and teachers: when we teach kids it is OK to be spied on, they will be less concerned with privacy in adult life too. Surveillance is a key feature of authoritarian regimes, and our world is increasingly moving in the wrong direction here. Don’t teach your kids it is OK for people to spy on them. Protect our democracies by teaching your kids to take care of their own privacy.
Next I asked him if he believed people could be spied on using their cell phones. The answer was “maybe”. I told him that they can but most parents don’t know how, and hopefully have no wish to do so. He has an Android phone – and I told him that I’ve made the settings on that phone such that it does not store his location data in a Google account but that most people who use Android never think about this. And the same goes for Apple. He was skeptical about this, so I told him I would turn on the “timeline” feature on my own Android, and show him later what the app stores on Google’s servers. Afterwards I showed him what they track (including where I was, how much time I spent where, the photos I’d taken, and the like).
Take-away points
- Think it through if you choose to turn on features like Google’s timeline. Or rather, think it through if you are not taking steps to turn it off – it is on by default.
- Guard your account’s security like a hawk; especially if you choose to use these features. Turn on two-factor authentication now.
- Talk to your kids about privacy. The habits they learn now is what they bring with them into adulthood. Teaching your kid about privacy is an important contribution to safeguarding democracy and freedom of speech.
- The example here was using Android phones. The story is the same on other platforms, and with other mapping and location based service providers than Google.
- If your password is leaked, change it immediately.
What do you think about this? Let me know in the comments! Especially – do you think it is OK to track your kids like the watch described above? Are you OK with Google and their competitors storing such detailed location data about you?



